
Decoupled Authentication – A Detailed Guide For 2023
Ritesh Shah
10 min read

There’s a new authentication method that doesn’t involve multiple sessions and endless redirections. It’s called ‘decoupled authentication.’ Sounds fancy, right? Well, it is — and it’s incredible!
This article will explore what decoupled authentication is and some of the benefits you can expect. So if you’re looking for an easy way to improve your website’s security, keep reading.
Introduction — Some Major Pain Points 🔎
Many customers complain about the number of steps typically required to complete online payments. In some cases, they abandon transactions altogether due to multiple unexpected redirections that confusingly occur throughout the website or app interface. This is even worse when using mobile devices to make a payment.
While having a smooth buyer experience is vital, focusing on security is equally essential. With data breaches and cyber-attacks becoming more common, protecting your company’s information is crucial. One way to do that is by using a particular type of authentication called decoupled authentication, often dubbed “the next big thing in payment security.” So you need to start thinking about decoupling payment systems if you want your business to be safe from cyberattacks in 2023.
This article will explain what decoupled authentication is and how you can use it in your business to enhance security and help customers with ease of transaction. Before doing that, let’s understand the fundamental difference between authentication and authorisation, two often confused terms in cyber security.
Authentication or Authorisation — What’s The Difference? 🧐
The difference between authentication and authorisation is like day and night.
Authentication is the process of recognising someone’s identity by confirming their credentials; in this case, it’s you, the user. In contrast, authorisations focus on what can be done once someone has been verified — usually restrictions related to permissions granted by a system (i.e., “you cannot access these files”).
The process of authenticating someone is something businesses do almost daily. Authentication can also be used for services and devices to confirm who you are when accessing these resources with your identity verified. The result will often give access (or otherwise affect) to a user’s permissions while using them.
Obviously, there’s a difference between authorisation (which focuses heavily on limiting how much power certain entities have) and authentication (looking out only at whether something seems believable), and here we’ll focus more on authentication and ways of implementing the decoupled architecture.
The evolution of authentication has been an exciting journey with many changes. The scope and priority have altered but are also located at a new stage within the identity life-cycle, meaning there’s so much we need to know.
Understanding The SSO Model & Application Silos 📋
Security is a massive concern for most businesses today, especially those that deal with customer data. To protect your company’s assets and keep hackers out, you need an effective way of authenticating users before they can gain entrance into any system or network which houses valuable information like financial records.
Sometimes it means having one app do all functions explicitly related to security measures. For example, signing up new clients/customers, account management, including sending notifications when someone reaches certain milestones within their subscription period, paying invoices from existing customers who haven’t participated previously, and making purchases online through third-party vendors.

One of the common ways of authentication is the single sign-on (SSO). It is a design pattern that allows you to log in once and access multiple applications with different login sessions. This means the same credentials can be used for any application within your company or organisation, but you’ll have to log in separately for each application.
To not have too many accounts set up at once (especially if they are all going through one central provider), SSO often requires users to enter their password each time an app wants them to log in. This creates a particular situation where each authentication is tied to an application or service, which is limiting for operational and security purposes. This situation is called “application silos,” — and it demands creating groups of applications or services with similar authentication requirements.
The IDP Model Of Authentication 💡
Authentication should be convenient and easy so that users can easily access their information, and the pattern needs to provide a range of options to authenticate different applications. That’s why there’s another authentication method that’s popular and well-documented. With the increasing number of people who are identity providers (IDPs), companies must take extra steps to ensure our networks and systems stay secure.
The most common way hackers invade these days is by using one-time passwords (OTPs) delivered via SMS or email instead of those old methodologies relying solely on passwords alone. They can also provide local tokens based on OAuth standards to get in. So you don’t even need your phone nearby when accessing sensitive data at work.
With push authentication, the IDP serves as a convenient way to ensure that your account is who you say it is without having an extra step of authenticating again later on. Biometric technology like fingerprints or faces can also be used for local verification, which means less time entering passcodes.
Here Comes The Decoupled Authentication! 🔨
The SSO and IDP models are popular technologies that provide an easy way to share data across applications. However, many vendors offer dedicated services for this purpose. That means it’s not just your company’s application that needs access rights but also any cloud or on-premise solutions you may want to use.
These services were confined within each business unit before, and now they span entire organisations because they’re moving away from relying solely upon app-level security measures towards securing federation boundaries. In this regard, a standard transaction using 3-D Secure can require an authentication challenge from the cardholder while shopping.
Decoupled authentication happens when the transaction occurs without the user being in session with the merchant via their website or mobile application. The user/cardholder may, in fact, not be present at all.
The 3D Secure 2 protocol has been updated with a brand-new feature that enables cardholder authentication without the customer interacting online. This means merchants can now request information from banks even when their customers are offline, and it will be up to those financial institutions whether or not they want to provide this service. This is called decoupled authentication.
It opens up many possibilities, such as making purchases while travelling abroad where they may otherwise not always be accessible due to differences between countries’ currencies. Furthermore, instead of requiring the customer to interact with your website or app while online shopping for payments, you’ll be able to get them verified through their bank straight away.
In this regard, decoupled authentication solves some of the existing customers’ pain points and security problems.
Decoupled Authentication — The Workflow 🌊
Here is how the decoupled authentication system works.
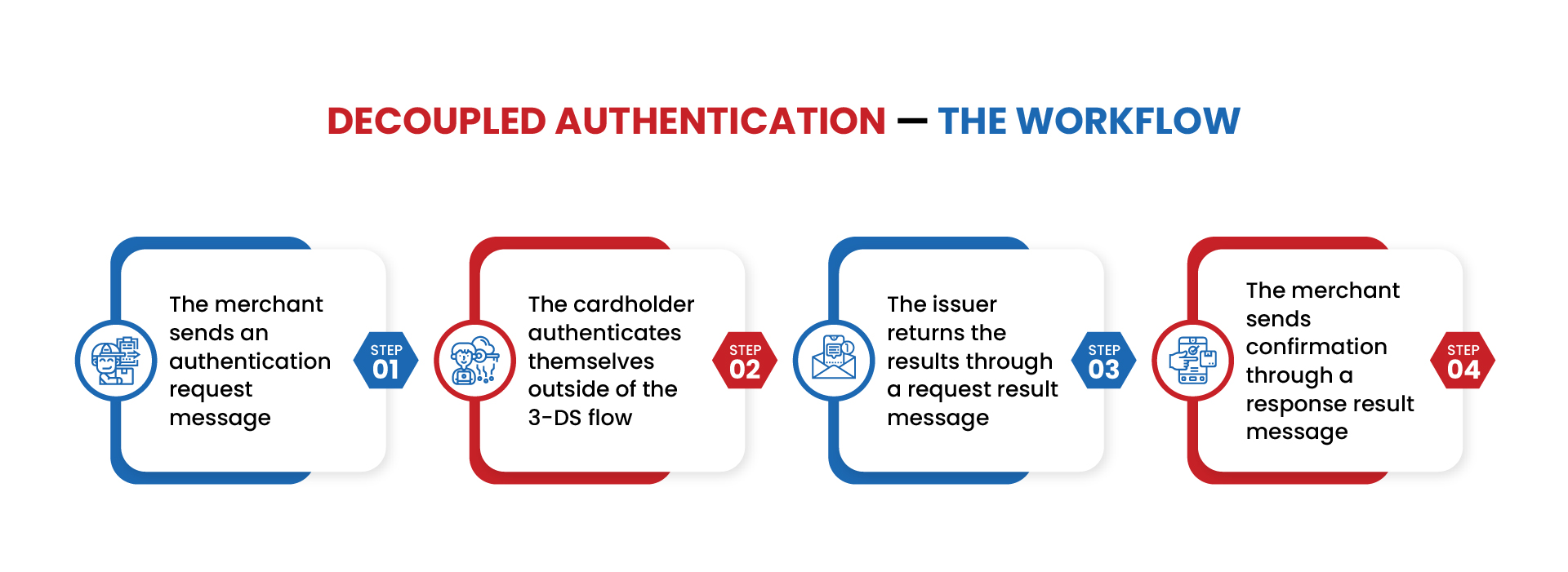
- The merchant sends an authentication request message and requests decoupled authentication. If the issuer supports decoupled authentication, the merchant will get a response from the issuer.
- The cardholder authenticates themselves outside of the 3-DS flow. The merchant can proceed with their transaction.
- After authentication, the issuer returns the results through the request result message.
- Finally, the merchant sends confirmation through the response result message.
The Need & Importance of Decoupled Authentication ✨
With decoupled authentication, the customer and merchant are separate entities. The customer may use a mobile app or visit an online site to make purchases without having their own session with that particular business — they only have access while browsing for items on either platform.
In other words, they can’t see what’s happening inside of someone else’s head!
Merchants can authenticate customers and process transactions without having direct access. They will receive an alert, typically through their phone’s notifications system or email account, that there is a request from another merchant for authentication (or payment consent). The merchant then has two options on how they want this handled: a) accept it as usual, b) or reject all future requests unless the customer provides additional proof of identity at first purchase.
Decoupled authentication is necessary because it protects merchants from fraud and liability even if the cardholder cannot provide immediate proof of their identity. This can happen when they are out shopping or busy with other things like kids at home. The benefit here also lies in verifying your customer‘s identity before completing transactions. It’s perfect for instances when the cardholder is not immediately available for authentication, and still, the issuer would like to authenticate the cardholder.
That’s where Stripe comes in — a payment gateway that allows decoupled authentication and additional verification with 3D security. Stripe also provides card payments without bank authentication, especially with the US and Canadian bank cards, and slowly they’re planning to scale for a global customer base. Please go through our most-read blog post on why Stripe is the best payment gateway to date to find out more about Stripe.
When Is Decoupled Authentication Used? 🤔
❇️ Mobile Payments
The 3DS software development kit (SDK) takes an approach where they do not want their own display elements shown but rather just show the issuer bank. This compares to what might happen with a mobile app that opts for requesting instead of rendering these things. This leads us towards decoupled authentication being more straightforward and cheaper since there isn’t any need within your application code base when working across multiple platforms.
❇️ Merchant-Initiated Transactions
To process merchant-initiated transactions (MIT), merchants who deal with card file payments or recurring income have a challenge from time to time. When this happens, sending an elegant decoupled authentication request can help complete your sale without having the customer come into town and waste their valuable business hours waiting in line while you handle other tasks like paperwork.
❇️ Payments Over the Phone
With decoupled authentication, calling centres or businesses can take payments over the phone without any risk for either party. They can also verify cardholders’ identities quickly and securely, which increases approval rates significantly, driving up MOTO (Mail Order Telephony) transaction costs.
The customer’s credit card information is being verified over the phone by a business, such as for reservations. In this case, it would be helpful to use decoupled authentication so that approval can happen in real-time. This occurs with just one call instead of waiting on hold or having an agent come out at their convenience later when they’re busy doing other things like making payments themselves.
Final Thoughts 🔥
So what is decoupled authentication? It’s a process by which the customer’s authentication occurs outside of their interaction with the merchant website or app. This can be done in various ways, such as through SMS verification or email-based confirmation. Merchants can set a time limit — ranging from minutes to up to a week — depending on how long the authentication may take.
An excellent first step would be to separate disparate systems. This will allow for easier maintenance and troubleshooting if something goes wrong in either platform or when they’re both being used at once, without having any potential conflicts between them because it’s not tied into one another so tightly.
If you want to learn more about this type of authentication and how it could benefit your business, write to us today! Our team would be happy to answer any questions you have and help you get started with implementing this security measure.
Topics
Published On
June 06, 2022

